
应粉丝要求为强大的ExploitPack出个Windows版教程
分析Linux版的Crack流程总结如下:
1、将exploitpack.com和www.exploitpack.com写入hosts文件
2、创建changelog目录、public和appversion文件,其中appversion文件中写入版本17.07(其实好像随便都可以)
3、创建一个exploitpack.com证书
4、为JDK导入安全证书
5、利用该证书启动https和http服务,指向public和appversion文件由于Exploit Pack启动后的验证流程分两步:
1、先请求https://exploitpack.com/changelog/public
2、再请求http://www.exploitpack.com/changelog/appversion那我们直接编写脚本代替我们执行Crack流程:
func main() {
// 修改hosts文件
hostsFile := `C:\windows\system32\drivers\etc\hosts`
hostsData := []byte("\n127.0.0.1 exploitpack.com\n127.0.0.1 www.exploitpack.com\n")
file, err := os.OpenFile(hostsFile, os.O_APPEND|os.O_WRONLY, 0644)
if err != nil {
fmt.Println("[!]Failed to open hosts file:", err)
return
}
defer file.Close()
fmt.Println("[+]hosts文件修改成功!")
_, err = file.Write(hostsData)
if err != nil {
fmt.Println("[!]Failed to write to hosts file:", err)
return
}
// 复制cacerts文件
javaHome := os.Getenv("JAVA_HOME")
cacertsPath := filepath.Join(javaHome, "lib", "security", "cacerts")
err = copyFile(cacertsPath, "cacerts")
if err != nil {
fmt.Println("[!]Failed to copy cacerts file:", err)
return
}
// 导入证书到cacerts文件
keytoolCmd := exec.Command("keytool", "-import", "-alias", "exploitpack", "-keystore", "cacerts", "-file", "server/crt.pem")
keytoolCmd.Stdin = strings.NewReader("Y\n")
err = keytoolCmd.Run()
if err != nil {
fmt.Println("Failed to import certificate:", err)
return
}
fmt.Println("[+]证书导入成功!")
// 移动更新后的cacerts文件
err = copyFile("cacerts", cacertsPath)
if err != nil {
fmt.Println("[!]Failed to move updated cacerts file:", err)
return
}
// Crack完成
fmt.Println("[*]Crack完成,开始启动...")
// 启动HTTP和HTTPS服务器的线程
go runHTTPServer()
go runHTTPSServer()
fmt.Println("[*]等待HTTP和HTTPS服务器启动...")
// 等待HTTP和HTTPS服务器启动
time.Sleep(3 * time.Second)
fmt.Println("[+]HTTP and HTTPS servers have started.")
// 设置使用特定版本的Java路径
javaPath := filepath.Join(javaHome, "bin", "java.exe")
// 运行ExploitPack.jar
cmd := exec.Command(javaPath, "-jar", "ExploitPack.jar")
// 启动进程并等待它退出
err = cmd.Run()
if err != nil {
if exitErr, ok := err.(*exec.ExitError); ok {
fmt.Printf("[!]ExploitPack.jar process exited with error: %s\n", exitErr.Error())
} else {
fmt.Println("[!]Failed to start ExploitPack.jar:", err)
return
}
} else {
fmt.Println("ExploitPack.jar process exited.")
}Linux下启动https和http服务很容易,Windows稍微麻烦些,但是写个程序就容易了:
type MyHTTPRequestHandler struct{}
func (h *MyHTTPRequestHandler) ServeHTTP(w http.ResponseWriter, r *http.Request) {
switch r.URL.Path {
case "/changelog/appversion":
w.WriteHeader(http.StatusOK)
w.Header().Set("Content-Type", "text/plain")
w.Write([]byte("17.07"))
case "/changelog/public":
w.WriteHeader(http.StatusOK)
default:
w.WriteHeader(http.StatusNotFound)
}
}
func runHTTPServer() {
server := &http.Server{
Addr: ":80",
Handler: &MyHTTPRequestHandler{},
}
err := server.ListenAndServe()
if err != nil {
fmt.Println("HTTP server error:", err)
}
}
func runHTTPSServer() {
server := &http.Server{
Addr: ":443",
Handler: &MyHTTPRequestHandler{},
}
err := server.ListenAndServeTLS("server/crt.pem", "server/key.pem")
if err != nil {
fmt.Println("HTTPS server error:", err)
}
}执行Crack效果如下,以前没开启过80和443端口服务的防火墙会提示确认: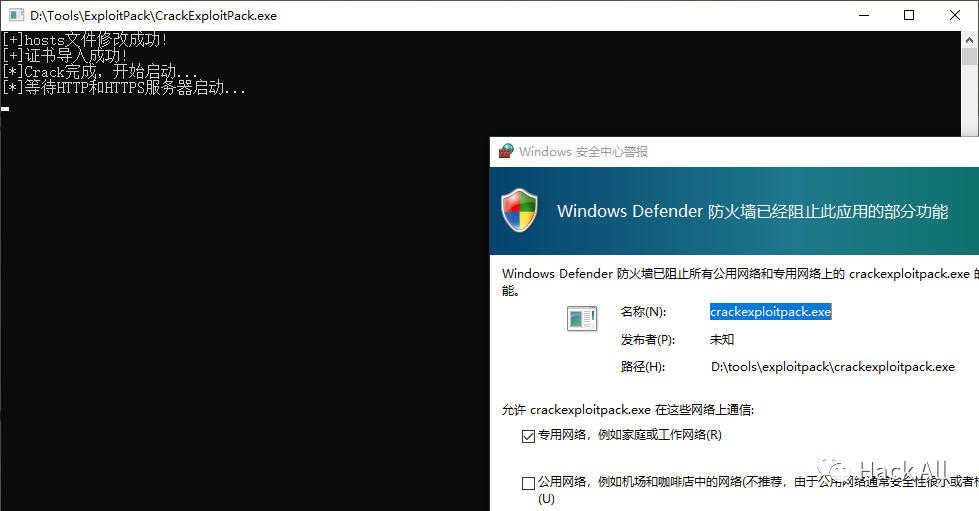
启动http和https服务后运行程序,开始读进度条:
出现版本信息,加载程序: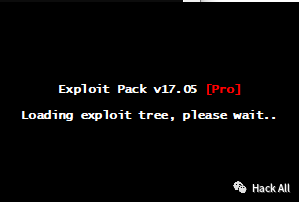
加载完成,进入主界面,可以开始享用了: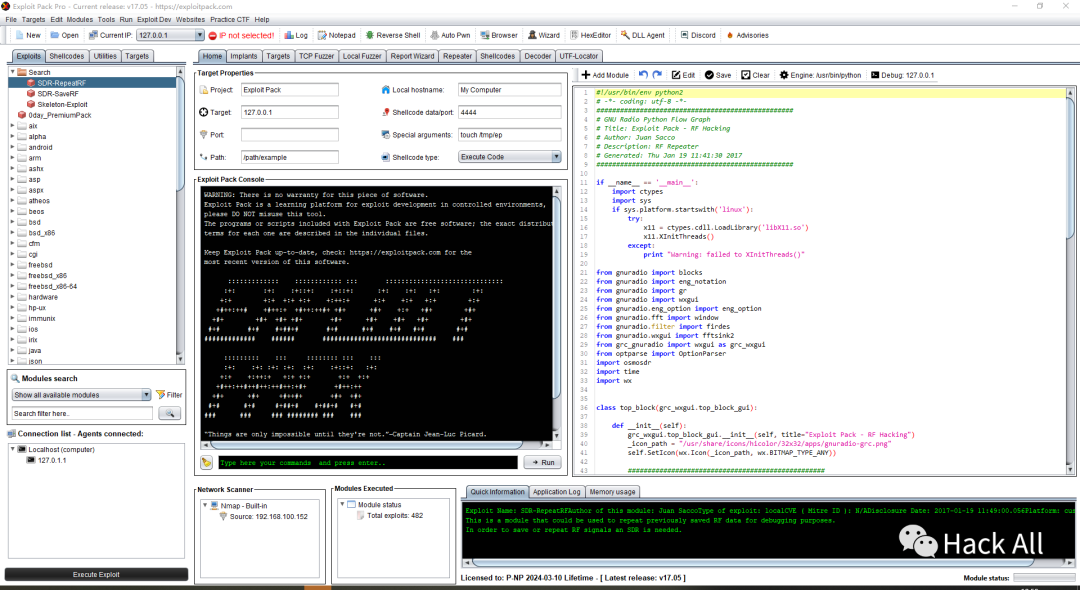
公众号后台回复20230609获取代码和程序!
Comments | NOTHING